We will talk about cross-site scripting (XSS) prevention basics. Take note, preventing a more advanced XSS attack is not covered in the blog. We will also introduce the advantage of using Web Application Firewall (WAF) over other web attack prevention.
XSS Prevention
There are many ways to prevent Cross-Site Scripting (XSS). First, Input validation – this is the process to block or sanitize input text with tags. Next, Escaping – this refers to the practice of encoding special characters as they interpreted literally and not a special characters. In short these characters won’t be executed as codes. Many modern Javascript framework automatically do escaping such as React, Angular2 etc. Other web frameworks such as Django also have built-in XSS attack prevention. There are also some cases that your application only take a handful of valid values. The best practice to only permit those known good values using whitelist model. Another attack prevention is to enable content security policy from the HTTP response header. You can instruct the browser to execute scripts only from the list of sources. So here’s the question what if you have this application that is vulnerable to XSS and it’s using an old insecure framework and there are too many complex code with complex server configuration and many web servers as well. You don’t want to change all of these!
Web Application Firewall (WAF)
Would it be good if you can centralize everything? The web server protection configuration and management, instead of changing various codes and changing all configuration of multiple web servers. This is where the Web Application Firewall (WAF) comes in. It’s policy-based, signature-based and it’s an intelligent appliance as it would automatically enable signature based on specified system, framework and programming languages.
F5 ASM vs F5 Advanced WAF
F5 Application Security Manager (ASM) is a security solution offered by F5 Networks, a company specializing in application delivery and security. It is designed to protect web applications and APIs against various security threats, such as web application attacks, data breaches, and unauthorized access. F5 ASM is rebraned as F5 Advanced WAF. It offers enhanced features and functionalities compared to the ASM module
Topology
We added an appliance in our topology there is now an F5 WAF between the two nodes. A WAF between the attacker and the target web server. First we’ll show you the F5 WAF security policy then the attacker will send an attack payload to the web server. Lastly, we’ll look at the result if the attacker is detected and mitigated.
F5 ASM/Advanced WAF Configuration
Here is a guide or steps to configure XSS Prevention:
- Access F5 Configuration Utility. Create or use an existing security policy. Go to VS configuration and under Security -> Associate the security policy.
- On the same page Enable Logging using Log all requests log profile
- Edit the Security Policy and Application Security -> Server Technologies. Verify Language, Framework, Database, OS etc are activated. In our case we enabled Django, Postgres. MyQL and Unix/Linux technologies.
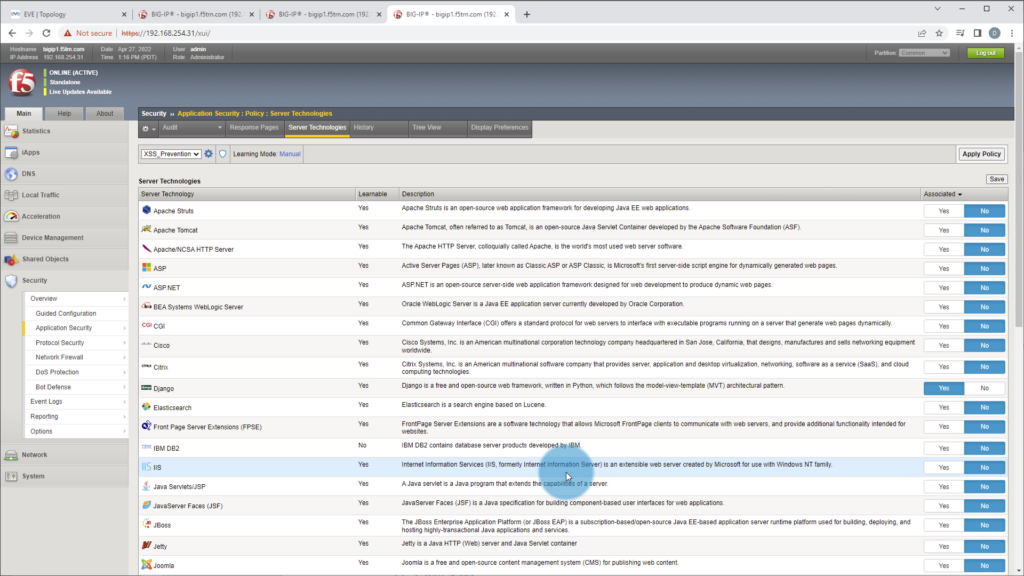
- By enabling Server Technologies, this enables signatures designed to protect those technologies selected.
- When a successful XSS is launched, you can check the logs by go to F5 Configuration Utility. Click Security -> Event Logs -> Applicaiton -> Request.
- It should detect an attack signature is detected and under occurrence. It displays the actual violation It provides the a keyword, attack signature details (XSS Script) and parameters.
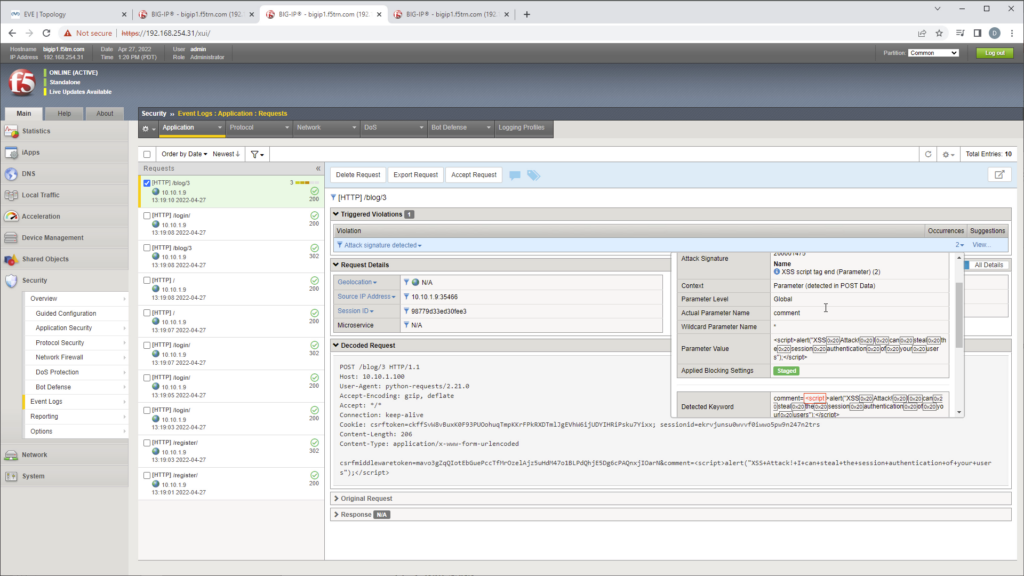
- By default it only detects (not Blocked) the attack violation as staging mode is still enabled.
- Go back to Security -> Application Security -> Policy Building -> Learning and Blocking Settings. The Enforcement Mode by default is set to Transparent (aka monitoring mode)
- Disable signature staging and change the enforcement mode to Blocking.

- On the same page, under attack signature you can verify that it’s still under signature staging. Which means it’s still under learning mode.
- Save configuration and click Apply Policy. Make sure you are using the correct Security Policy.
- Launch XSS, it should be blocked by F5 ASM/Adv WAF.
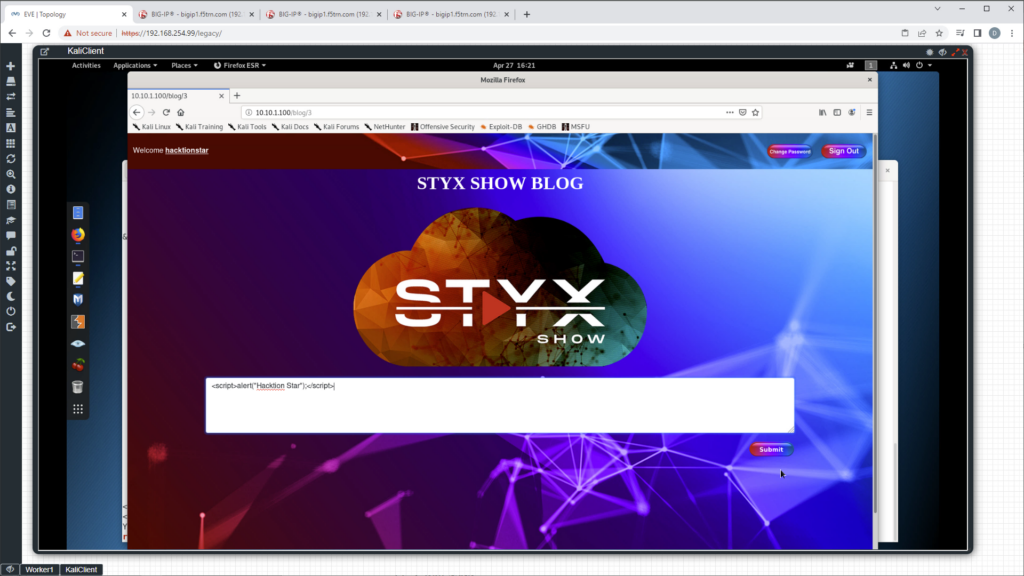
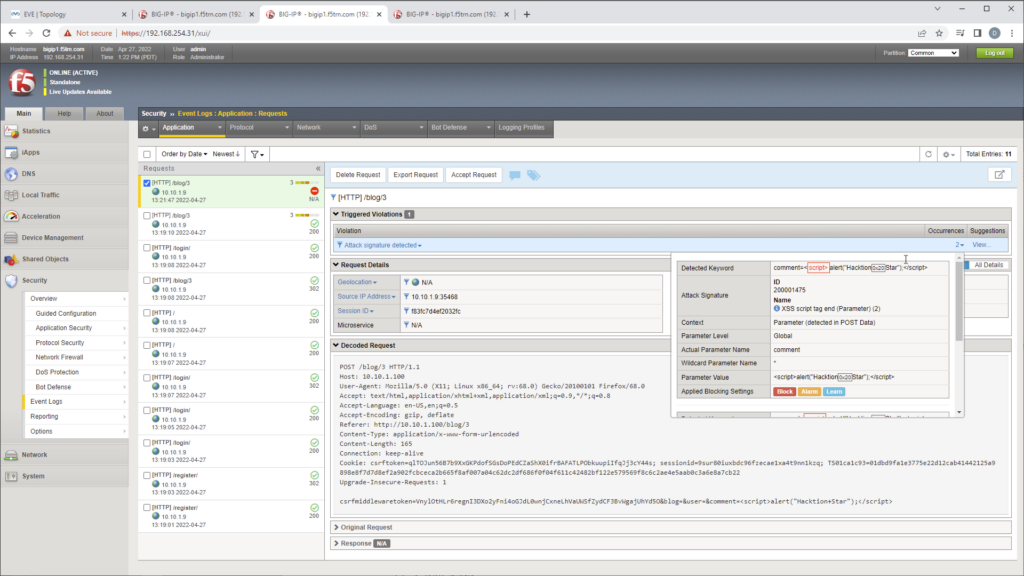
- Go back to F5 Configuration utility and click Security -> Event Logs -> Application -> Request.
- You should see the HTTP request was blocked XSS violation.
Click below to access the video version and consider subscribing.
Hi, this is a comment.
To get started with moderating, editing, and deleting comments, please visit the Comments screen in the dashboard.
Commenter avatars come from Gravatar.